Terraform deploy system
Terraform is an infrastructure-as-code tool that allows you to define both cloud and on-prem resources in human-readable configuration files that you can version, reuse, and share. CiviForm provides Terraform configuration files that allow you to deploy CiviForm on AWS. Knowledge of Terraform is not required to run them, but reading the high-level Terraform overview may be useful.
More detailed information on our deploy system can be found in our developer docs.
Setup
Outside configuration
You will need some values that are configured outside of CiviForm before you start the setup. Some of the steps are optional, meaning that you can bring up a staging environment and get the app working without them, but they will need to be completed for production setup.
(Optional) Admin auth client_id, client_secret, and discovery_uri. See setting up Azure AD for an example
(Optional) Applicant auth client_id, client_secret, and discovery_uri. See setting up the Authentication Providers
Domain name for your deployment. For example
civiform.mycity.gov(AWS) ARN of an SSL certificate for load balancer. See requesting AWS certificate
(AWS) Decision around where deployments will live. See AWS deployment setup options
Steps to run
Fork the civiform-deploy repo to your organization via the GitHub webpage.
Clone the repo onto the machine you are deploying from. Ideally, this would be a shared instance that multiple people can log onto.
Find the version that you want to deploy on Github.
Copy the
civiform_config.example.shintociviform_config.shand fill out the missing values. You can get a sense of required values depending on your cloud provider by looking at staging-aws configs.Run
bin/doctorand install the dependencies.Run
bin/setup. What to expect:Takes up to 20 minutes to run. Make sure you have time to allow the script to run to completion to avoid errors.
Terraform brings up resources in the cloud (database, network, server, etc).
Asks confirmation a few times before creating resources, listing everything that will be created.
Safe to re-run the script if it fails (re-runs will take longer because resources must be destroyed before being re-created).
The configuration values in
civiform_config.shrepresent the desired state of your CiviForm deployment. Thebin/setupandbin/deploycommands work to make your cloud environment match the desired state. If a command fails, your cloud environment may not match the desired state. These commands are safe to retry if they fail. If a command is persistently failing, you can work with our on-call engineer to resolve the issue. Our on-call engineer responds to new issues in the CiviForm issue tracker.
Note: If you are running bin/doctor or another command for a config file other than civiform_config.sh, you can specify that with the config flag (i.e. bin/doctor --config=civiform_staging_config.sh)
Deploy
Find the version that you want to deploy on Github.
Update the
CIVIFORM_VERSIONvalue inciviform_config.sh.Run
bin/deploy.
Rotating the application secret
The Play Framework used by CiviForm utilizes an application secret key. This key is used for signing session cookies and CSRF tokens, among other things. While this secret is secured storely by the deployment system, it's a good idea to rotate it periodically in order to mitigate the risk of a leaked secret.
IMPORTANT: When the secret is rotated, all user sessions will be invalidated. This means that any guest users in the middle of an application that have not submitted it yet will lose that application, and any logged in users or admins will get logged out. It is recommended that this rotation happen at a low traffic time of day. You may also want to give users a warning before it happens.
To rotate the secret, run bin/run, and enter the rotate_app_secret command. This will redeploy CiviForm, changing the secret key to a new, random value.
Additionally, you should add export RANDOM_PASSWORD_LENGTH=64 to your civiform_config.sh file. The secret length was originally only 16 characters, and when CiviForm moves to using version 2.9 or later of the Play Framework, 32 will be the minimum.
Troubleshooting
Terraform fails with error "Provider produced inconsistent final plan"
This error can happen when running bin/setup for the first time. If you see it, re-run bin/setup. This is a known Terraform bug.
Terraform fails with other errors
The deploy command is idempotent, so if it fails, try running it again. The setup command can also be re-run, but it may fail to destroy resources if the resources Terraform uses to track created resources are corrupted. If the script is failing to destroy resources, try running bin/run destroy on its own. If this fails, you may need to manually delete resources in your cloud provider's console. Once all resources are cleaned up, run bin/run destroy_backend_state_resources to cleanup up the corrupted backend state resources and then try running bin/setup again.
If changes were made upstream, you can change the code in the checkout env, but will need to commit PRs to fix in the main repo.
No such file or directory
If you see error like "no such file or directory"
The scripts expect you to be in specific directories. You probably need to cd into the checkout directory or the top level directory. If you are running setup/deploy/revert, you will need to be in the top level directory. If you are running a script like db-connection, you need to be in the checkout directory.
Terraform fails with Error acquiring the state lock
Error acquiring the state lockThis situation can happen when exiting deployment scripts using "Ctrl-C". Terraform acquires a lock every time you run ./bin/deploy or ./bin/setup, and releases the lock at the end of the script. This helps to prevent concurrent infrastructure changes. If the deploy process exited outside of Terraform, the lock remains and needs to be force removed in order to run deploy again. The end of the error message will contain the LOCK_ID. To unlock, re-run either bin/deploy or bin/setup with FORCE_UNLOCK_ID set like this:
Alternatively, it can be done by manually calling terraform like this:
(AWS) Notes on using CloudShell for deployment
It is an option to use CloudShell for doing deployments, but you should be aware that installations aren't persisted (see (FAQs)[https://aws.amazon.com/cloudshell/faqs/]), so it may be easier to use the AWS CLI.
If you do choose to use CloudShell, you likely will need to install Java and Terraform.
Java can be installed with sudo yum install java and terraform can be installed by following the installation commands under Linux / Amazon Linux.
Helpful resources
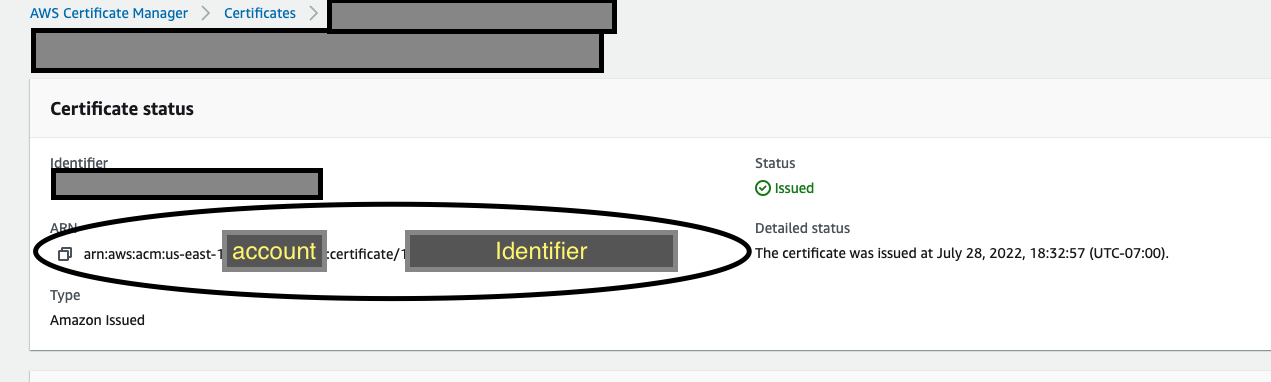
Requesting AWS certificate
Follow official documentation. After your certificate is ready and validated, copy the ARN from your console and put it into the SSL_CERTIFICATE_ARN variable in your civiform_config.sh
ARN has format of arn:aws:acm::<user_id>:certificate/<identifier>
AWS deployment setup options
Before going through the AWS deployment, it is helpful to understand how you plan to manage various deployments, if you plan to create multiple instances of CiviForm (i.e. staging, prod, etc.).
By default, each deployment will have its own prefix, which allows you to distinguish the different ones from each other, but AWS Organizations is a way of keeping deployments more separate from each other.
Some benefits of using AWS environments are:
There is more separation between environments, which makes it easier to remove resources without worrying about causing any issues to another deployment environment
It is easier to see cost breakdowns by deployment
A drawback to be aware of is that you'll have to create profiles in the AWS CLI and switch between the different profiles when doing deployments or, if using CloudShell, you'll have to do this in separate CloudShell for each environment.
Setting up Azure AD
The setup script prompts you to set up Azure AD. There are a few additional steps.
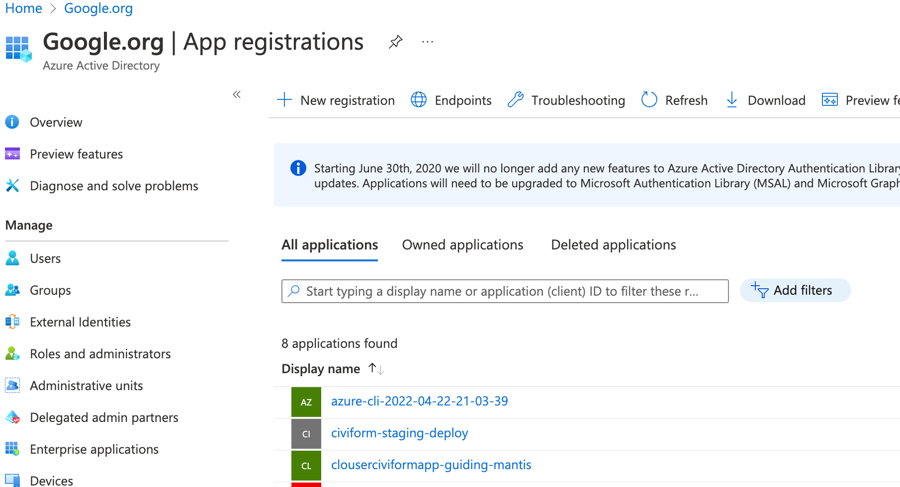
In Azure Portal:
Go to Azure Active Directory -> App registrations
Click the tab for "All applications"
Find your app (staging-dynamic-heron for CiviForm Azure Staging)
Use the menu on the left:
Authentication: setup the Redirect URI to be what the app expects: https://<custom_hostname>/callback/AdClient.
You will also need an admin group which creates CiviForm admins
Token configuration: To allow for CiviForm admins, you need to have Azure AD return the groups claim. Add the security groups claim (you can verify the groups claim is being returned by decoding the base64 token from the token you get back from Azure AD on the website-- if you preserve the log in the Chrome Dev Tool window it should be from https://<custom_hostname>/callback/AdClient)
Access the database for emergency repair
The CiviForm deployment system provides a mechanism for temporary and secure direct access to the production database via the pgadmin
For details on how to access the database with pgadmin visit the Production Database Access page.
Last updated
Was this helpful?